QE Touchstone
Giving a “single pane of glass” view of your security controls & capabilities, QE Touchstone identifies emerging threats, existing vulnerabilities & cyber risks, not only for your business but also for associated third-parties.
Internal Tool Overview
QE Touchstone, Quantum Evolve’s innovative approach to Cyber Resilience & Posture, provides your business with a comprehensive understanding of the technical, financial & compliance-related cyber risks within its digital ecosystem.
Allowing for full visibility into your organisation's cyber risk landscape, this platform provides real-time insights, assessing vulnerabilities, threat exposure, and compliance gaps across your systems. With intuitive analytics and detailed reporting, it enables proactive decision-making to mitigate risks and strengthen your overall security posture.
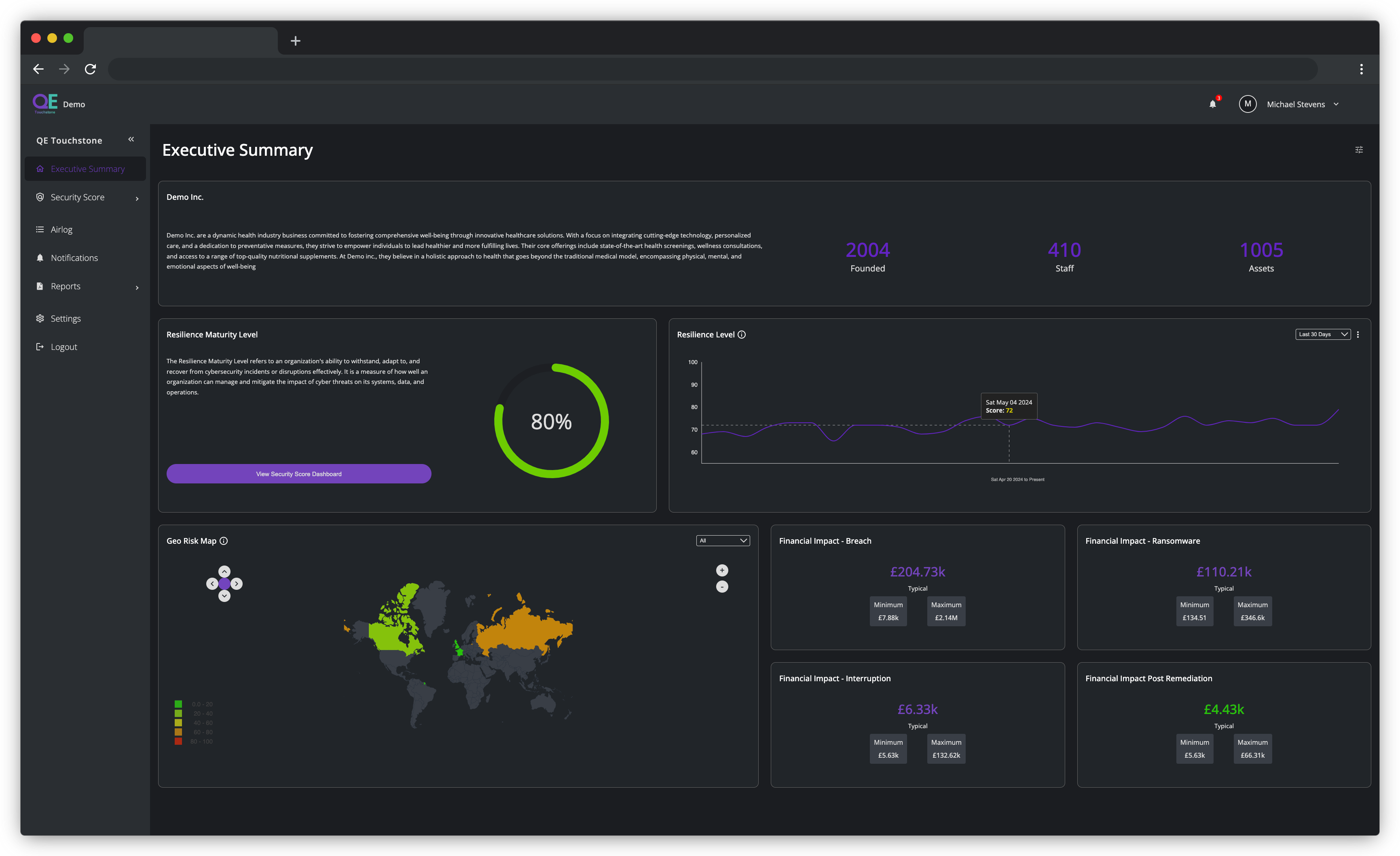
Risk Exposure Assessment
The unified risk view results in a complete, bespoke, prioritised risk-based remediation plan enabling you to understand & easily interpret your business' risks & cybersecurity maturity. Continuously Assess, Monitor & Protect with the QE Touchstone service.
Going beyond static assessments, we offer continuous monitoring of your cyber risk environment. QE Toucnstone tracks and evaluates potential threats in real time, identifying emerging vulnerabilities and alerting you to changes in your risk profile. With automated updates and dynamic risk scoring, you can respond swiftly to new threats, ensuring your organisation's defenses are always up to date and aligned with evolving cyber challenges. This continuous vigilance helps maintain a resilient security posture, reducing the likelihood of breaches and minimising potential impacts.
Flexible Module Selection
Our modular software application is designed with flexibility in mind, allowing you to customise the platform to fit your unique business needs. Each module focuses on a specific risk area, such as Domain Risk, Cloud Infrastructure Risk and Security Controls Risk, enabling you to choose and integrate only the functionalities you require. Whether you're looking to start small and scale up, or need a comprehensive solution right away, our modular approach ensures that you get exactly what you need, when you need it, without the clutter of unnecessary features.
Data Management
Without a clear and complete understanding of your IT estate, it is not possible to secure a business.
Data and Asset Discovery are critical components of effective cybersecurity and regulatory compliance.
Invest in these capabilities and better understand your IT estate, manage your risks, and respond quickly to security incidents.
Contact us to discover how Quantum Evolve can safeguard your business and aid the improvement of its business processes by detecting potential vulnerabilities and active threats.
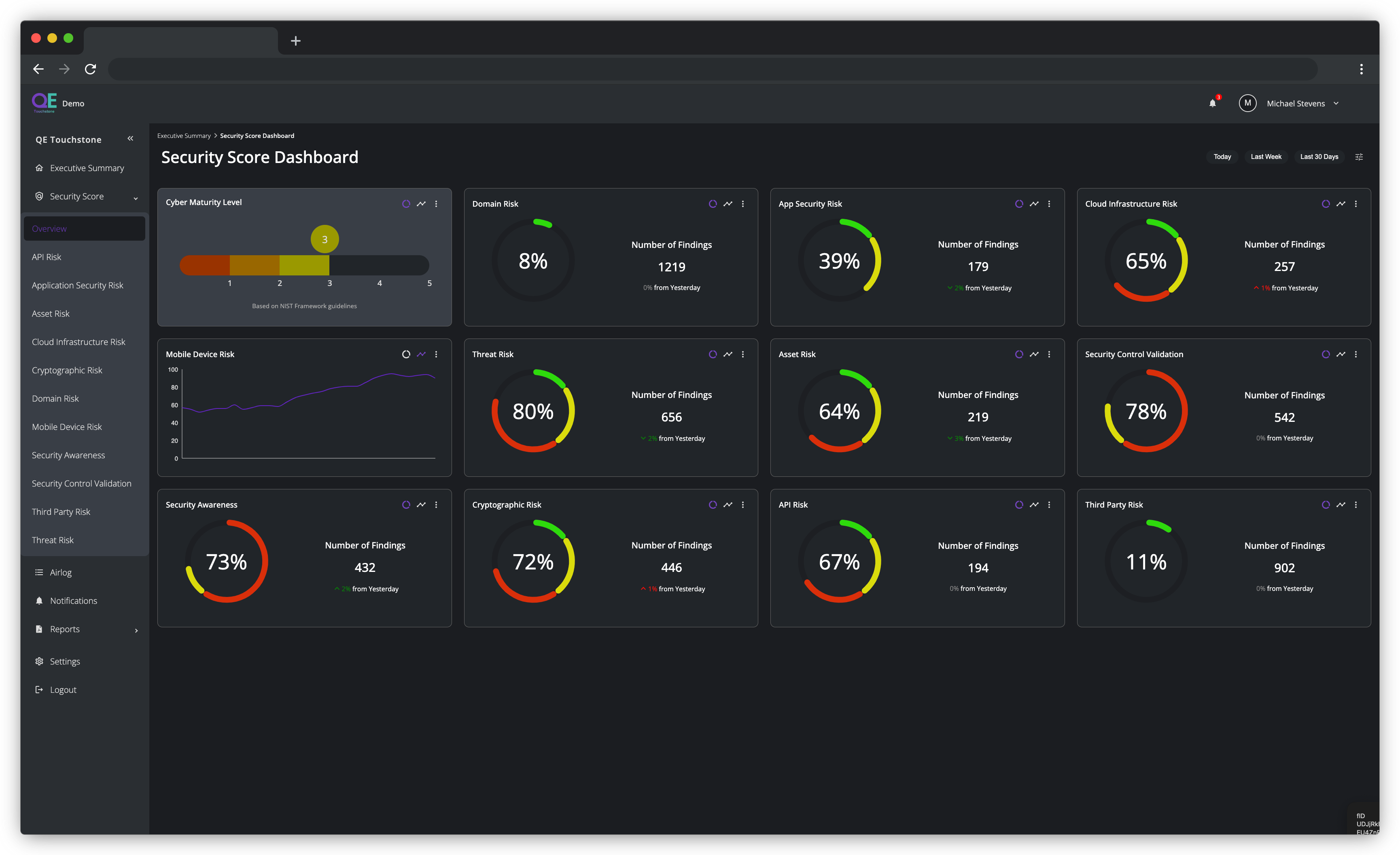
Domain Risk Assessment
By simply entering an organisations top level domain (TLD) such as Computacenter.com, our technology will discover all related sub-domains. All domains are validated against known vulnerabilities, misconfigurations, website issues, cryptographic weaknesses etc. which in-turn, provides a complete picture of where the issues are and how to correct them.
Get in touch for your Domain Infrastructure be evaluated for vulnerabilities, weaknesses, and entry points for an attacker with confirmation of any exploits that have been attempted and found to be successful.
API Risk Assessment
Risk is evaluated for websites and API usage due to their exposure to the internet, increased attack surface, constantly changing threat landscape, complexity of web applications, and handling of sensitive data.
Businesses that use websites and APIs need to be aware of these risks - Contact Quantum Evolve to ensure your systems are secure with our easy-to-understand risk-based remediation plan.
Threat Assessment
Regular and continuous threat assessments are critical for businesses as cyber threats are becoming more common and can result in significant financial and reputational damage.
Quantum Evolve’s Threat Assessment module helps you identify and understand potential cybersecurity risks and vulnerabilities in your business’ systems and applications.
This proactive approach can help prevent data breaches, cyber-attacks, and other security incidents, in addition to helping businesses comply with regulatory requirements and industry standards, such as GDPR, PCI DSS, and others.
Contact us to discover IoCs (Indicators of Compromise) and provide real-time threat hunting for signs of network compromise, data breach and exfiltration, as well as benchmarking your environment against CIS (Centre for Internet Security – a recognised industry standard).
Asset Risk Assessment
Asset Risk Assessment is crucial for your business because it helps you identify and prioritise risks associated with your hardware devices, software applications, and other digital assets.
Maintain visibility and control over your digital environments, and ensure they are protected against the latest cyber threats.
Contact us to obtain Quantum Evolve’s up-to-date threat intel on your known vulnerable assets.
Mobile Device Assessment
Mobile devices should be assessed to enable the protection of sensitive information and prevent unauthorised access to company resources.
Quantum Evolve Mobile Device Assessment identifies existing threats, vulnerabilities, assesses application risk and the most attacked users, devices and networks.
Contact us to find out which users, departments and / or devices present the biggest threat to your business and enable your understanding of why and how to reduce the risk.
Cyber Awareness Assessment
Phishing attacks are responsible for many successful cyber attacks.
They continue to be a major threat and it's critical to business to conduct regular assessments and training to mitigate this risk.
Contact us to prevent cybercriminals from gaining unauthorised access to your digital assets and sensitive information, and identify which users or departments require additional training, and what advanced threat protection you may require.
Cryptographic Assessment
A Cryptographic Assessment is important to maintain the security and integrity of digital communications and transactions and to protect against unauthorised access and data breaches.
Quantum Evolve discovers and validates your digital certificates which may cause a service outage.
We enable your business to reduce malicious usage of data encryption, data exfiltration and lateral movement of attackers against your public and private (SSH) and encryption (PGP) keys or cause.
Contact us to discover if your business’ cryptography (via algorithms, ciphers, and code) is permissible and protect your company and customer data by ensuring your information and communication is safe, secret and secure
Application Security Risk Assessment
Applications are complex and constantly evolving, making it difficult to ensure their security. They are primary targets for cyber-attacks, handle sensitive and confidential data such as personal and financial information and are subject to various compliance regulations like GDPR.
Contact us to assess the security, configuration, vulnerabilities, and compliance of your software applications.
Security Control Validation
Servers, Desktops and other endpoints are vulnerable and susceptible to hackers due to a lack of security controls.
Testing your business’ configurations, security controls and incident response is needed to understand how protected your business really is at the endpoint level.
Contact us to understand your business’ Cyber Resilience against cybersecurity threats and response to Ransomware and other real-life cyber-attacks.